Configure SAML / SSO Settings
Security Assertion Markup Language (SAML) is a protocol for web browser Single Sign-On (SSO) that uses secure tokens. Watch My Domains SED v4 supports SAML for select providers by default and you can add support for other providers easily.
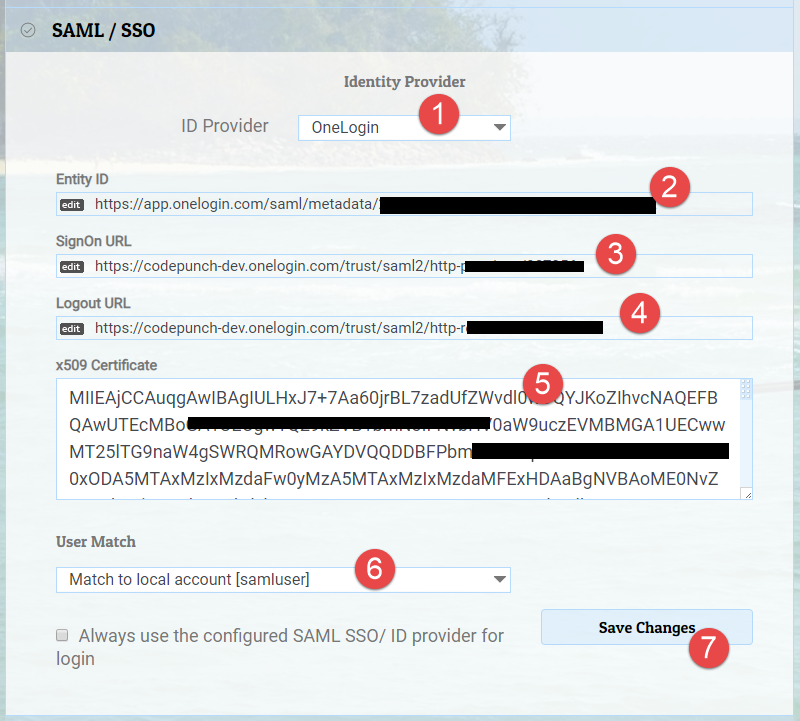
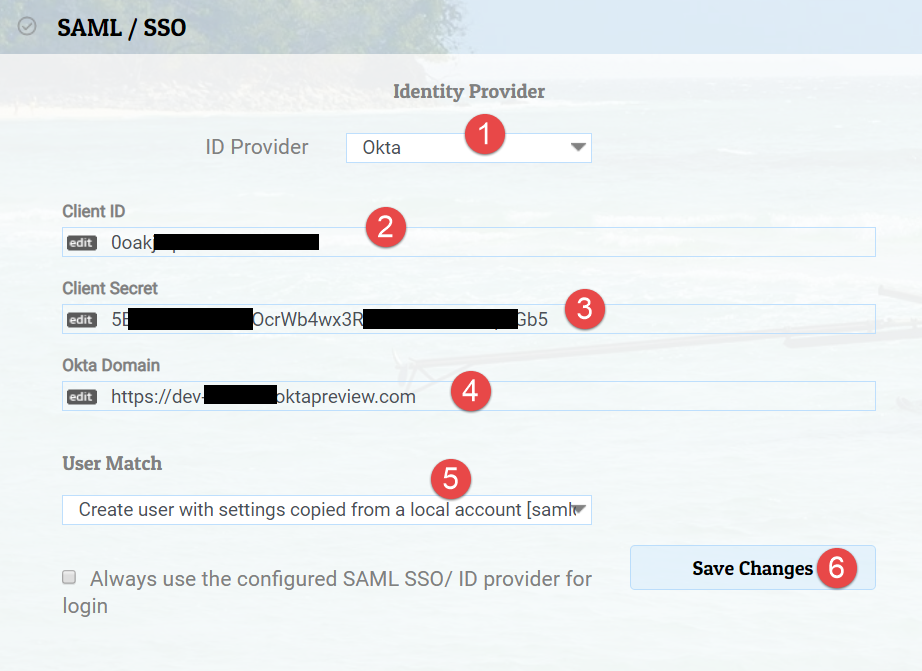
Application Details at Identity Provider
When you configure the application (watch my domains) at the identity provider, you will be prompted to enter details like Recipient URL, ACS URL, Single Logout URL etc. This is typically saml.php at the root URL of the Watch My Domains SED installation. For example, if the Watch My Domains SED application is installed at
https://domains.yourdomain.com/
The recipient URL will be
https://domains.yourdomain.com/saml.php
For ACS (Consumer) URL, use
https://domains.yourdomain.com/saml.php?acs
For Single Logout URL, use
https://domains.yourdomain.com/saml.php?sls
User Match
You can match new users from your Identity Provider to Watch My Domains SED by using three different methods.
Match to an existing local account
Create a user called samluser in Watch My Domains SED and select the
User Match setting to Match to local account [samluser]. Please make sure that
the local account (samluser) has the correct access rights because any unidentified
user from your SSO identity provider will get the same rights.
Create a user automatically
Create a user called samldefault in Watch My Domains SED and select
Create user with settings copied from a local account [samldefault] in User Match.
This will cause a new user to be created whenever the Identity provider returns with a
user unidentified by Watch My Domains SED. Please make sure that
the local account (samldefault) has the correct access rights.
Disallow logins from unknown users
If you select this option you will have to ensure that all valid users are already created in Watch My Domains SED and the SSO provider will return with a user id / email that matches the user name in SED.
SAML / SSO as default Authentication
You can check the box labelled 'Always use the configured SAML SSO/ ID provider for login' to use SSO by default.
Use the ?native to force a local login if the above setting is in effect. For example,
https://example.com/wmdsed4/?native
... will allow you to login using native authentication.
